Unveiling the XZ-Utils Backdoor

I was just looking into the latest exploit in xz Utils - an open-source data compression utility ubiquitous on nearly all Linux distributions - in which a backdoor has been found in the upstream tarball archives of xz (version >= 5.6.0).
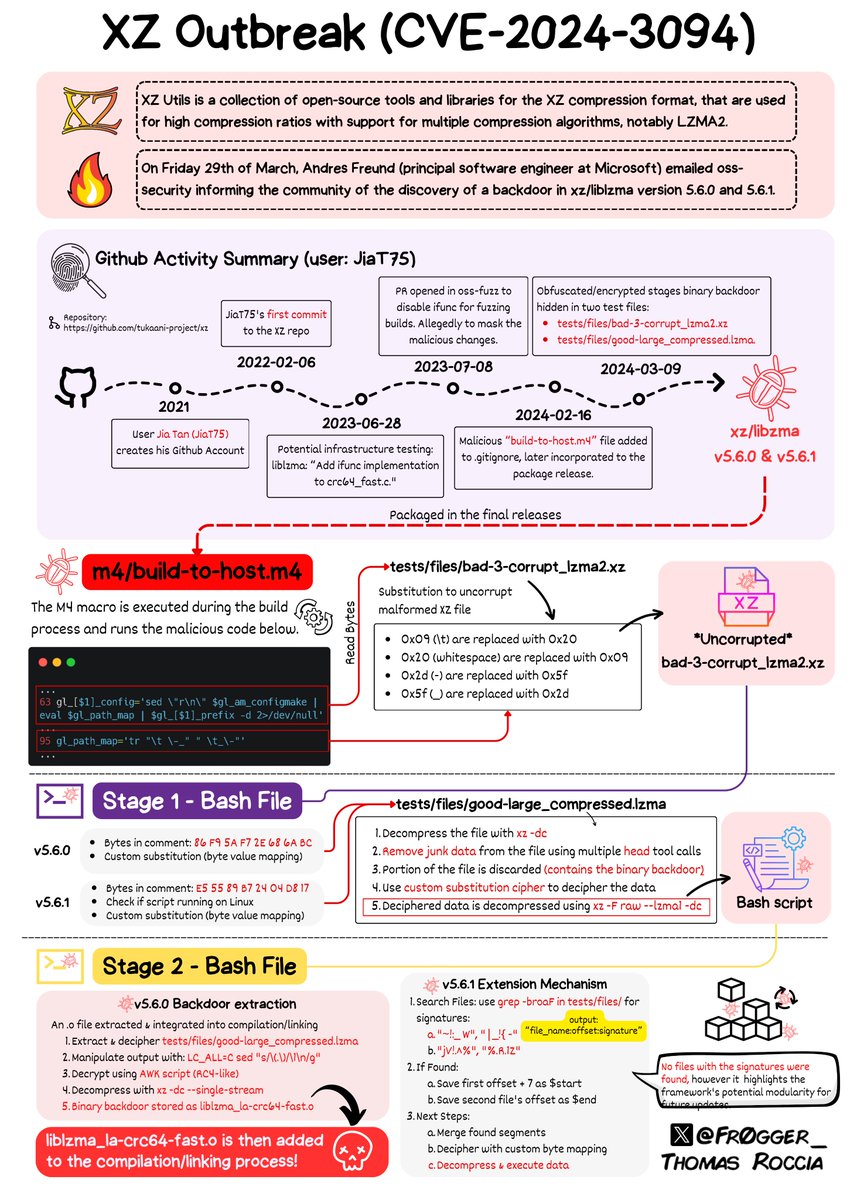
Through a series of complex obfuscations, the liblzma build process extracts a prebuilt object file from a disguised test file existing in the source code. This file is then used to modify specific functions in the liblzma code. As a result, a modified liblzma library is produced that can be used by any software linked against it, intercepting and modifying the data interaction with this library. - NIST Description
TL;DR: In short, it allows somebody with the correct private key to take over sshd, the service responsible for making SSH connections.
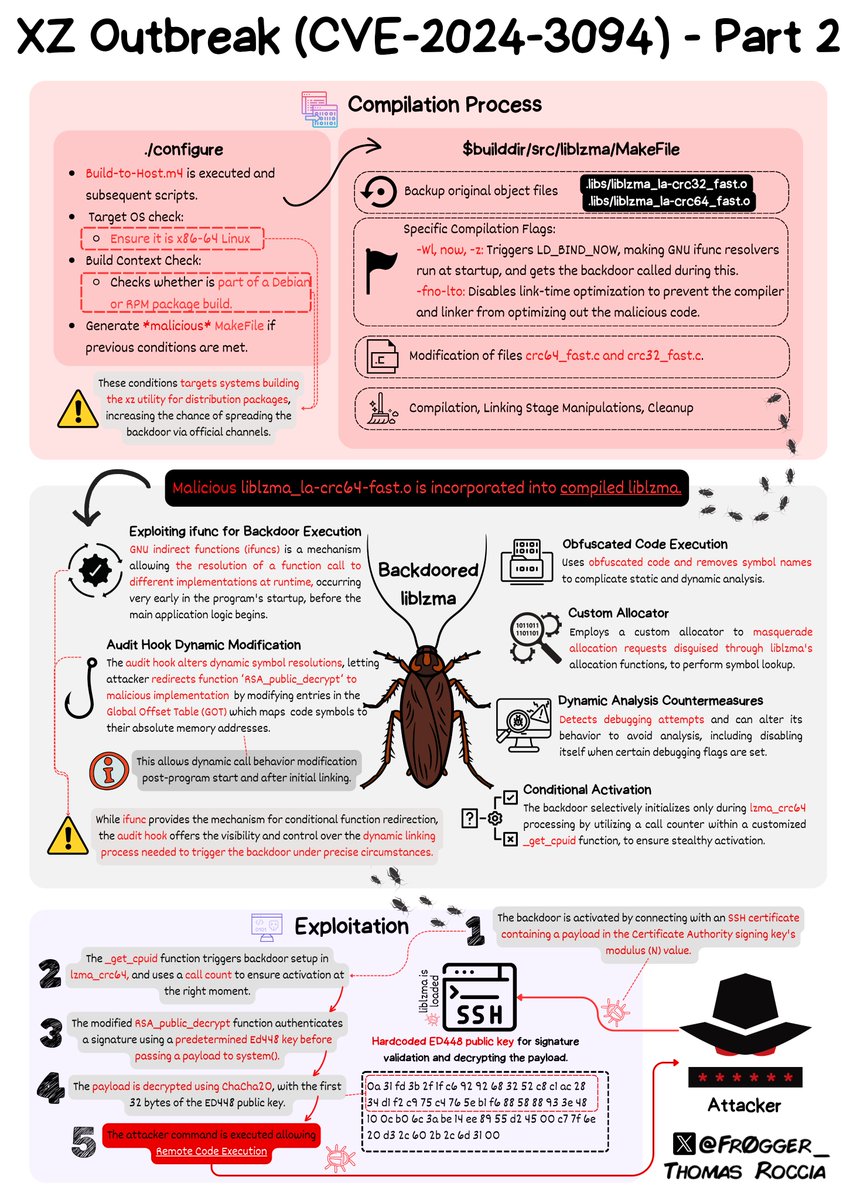
It's really a non-fictional real-life scenario of a supply-chain attack. And all of this was discovered because a researcher at Microsoft happened to notice that the time their SSH connection took to form was a bit longer than usual. It makes you wonder what else is out there.
References:
